Organizations Are Drowning in Security Issues
Security teams are inundated with the deluge of vulnerabilities and lack a clear remediation process.
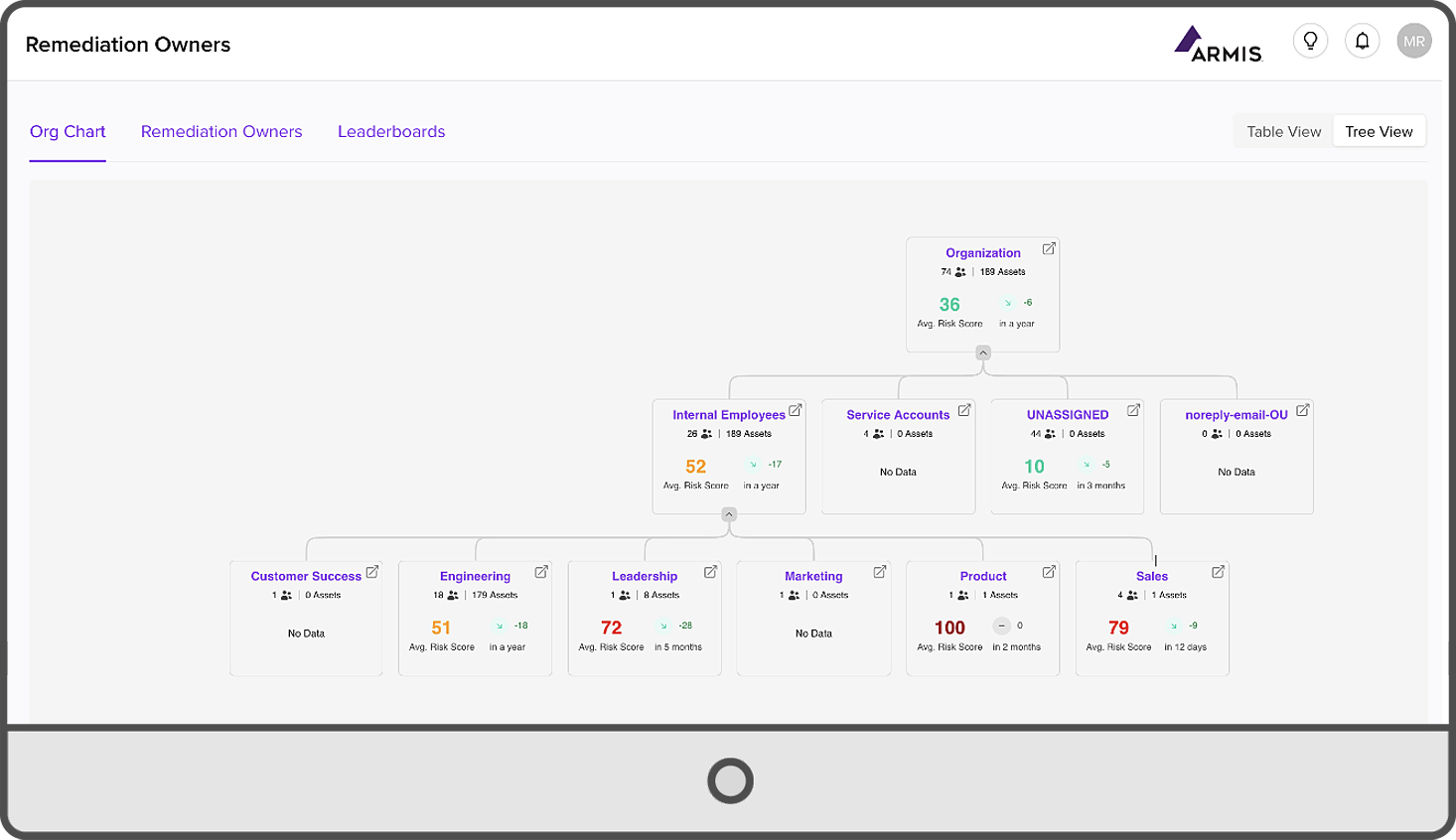
A Question of Ownership
Remediation efforts go beyond handling just vulns to addressing a host of other security issues that put organizations at risk. Are you still relying on a “round robin” assignment methodology to assign remediation tasks to whomever is “next up” on the list?
Still Using Spreadsheets?
Hackers are using AI to launch attacks. Manually downloading, correlating, and normalizing data from various point security products is not an appropriate counter response.
Lack of Adoption
Investing in automation and tooling, and establishing clear ownership and accountability for security is not always sufficient. Siloed teams and lack of collaboration can hinder the adoption of remediation best practices.
Armis Centrix™ for VIPR Pro – Prioritization and Remediation

AI-driven Predictive Capabilities
What to fix, who to assign, and how to prioritize
Leverage AI-driven predictive capabilities to determine who is most likely responsible for the asset and the remediation. Assign ownership for prioritized fixes based on automated mapping, with ongoing AI-based refinement based on operations feedback.
Integrate With Existing Workflows and Tools
Rather than simply pushing a detection tool’s finding into a ticketing tool, Armis generates a clear and concise recommendation, with a reason for the remediation request – such as a ‘high severity threat on an internet accessible asset’ to the right owner using the right workflow tool. Choose from a wide variety of integrations such as JIRA, ServiceNow, Zendesk, and many more.
Predictive Issues Ownership
When ownership is not clear, remediation efforts can fall through the cracks. Leveraging AI technology, Armis Centrix™ for VIPR Pro – Prioritization and Remediation predicts and assigns the correct owner by using advanced embedded workflows to manage and monitor exceptions, track progress with workflow tools and measure the effectiveness of the remediation process.
Regional Healthcare Provider Creates a Single Source of Truth from Multiple Data Feeds
Armis helps set the foundation for a strong security program
Armis has substantially shortened remediation time for potentially compromised devices. “Typically, Armis provides us with the visibility we need to remediate an asset in about one minute. In the past, tracking down the device and pulling in the network data would take us a minimum of two hours or more,” security leadership estimates.
Security Leadership
Regional healthcare provider
Additional Resources
2023 Gartner Market Guide for Vulnerability Assessment
According to Gartner “Vulnerability Assessment solutions identify, categorize and prioritize vulnerabilities as well as orchestrate their remediation or mitigation.” Read the report to see the Gartner report’s recommendations for Security and Risk Management leaders and why Gartner recognizes Armis as a Vulnerability Assessment leader.
2023 Quadrant SPARK Matrix™ for Vulnerability Management Report
This report includes a detailed analysis of the global Vulnerability Management solution market dynamics, major trends, vendor landscape and competitive positioning.
Solution Brief: Armis Centrix™ for VIPR Pro – Prioritization and Remediation
Modern organizations are grappling with a barrage of security alerts and scaling the prioritization and remediation process to secure the attack surface. Armis Centrix™, addresses the gap in cybersecurity between security findings and actionable remediation.

