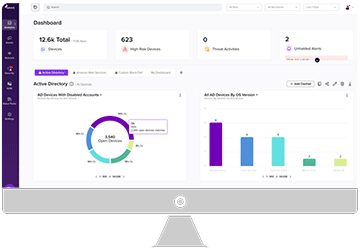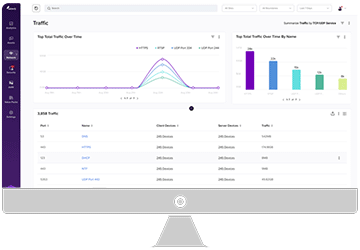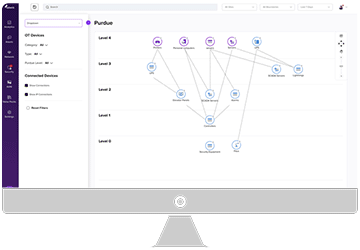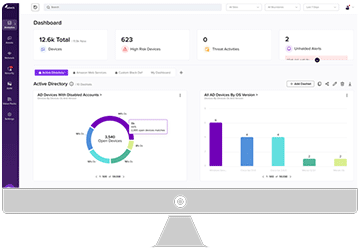
Armis Centrix™, the cyber exposure management platform, protects the entire attack surface and manages the organization’s cyber risk exposure in real time.
Watch the VideoAre You in Control of Your Entire Attack Surface?
Let’s spend some time together to explore the power of Armis Centrix™. Together we will:
- Talk about the challenges you’re facing in managing your attack surface
- Uncover those assets you didn’t know were there, or any other problems that prevent you from understanding your cyber risk exposure
- See how Armis Centrix™ can help address those challenges
Let’s talk!
““The most useful part of Armis Centrix™ when it comes to OT is its ability to do raw network analysis. But that’s not everything that Armis Centrix™ does, it also uses integrations and can collect data from our existing tools.”

Awards
Armis is proud to be recognized as a leading Cyber Exposure Management Platform.
See All Awards







