What is CVE-2024-11120?
CVE-2024-11120 is a critical OS Command Injection vulnerability affecting certain end-of-life (EOL) GeoVision IoT surveillance devices, including the DSP LPR, Video Server, and DVR product lines. The flaw arises due to insufficient input validation, allowing unauthenticated attackers to inject and execute arbitrary system commands.
When Was the Vulnerability Discovered?
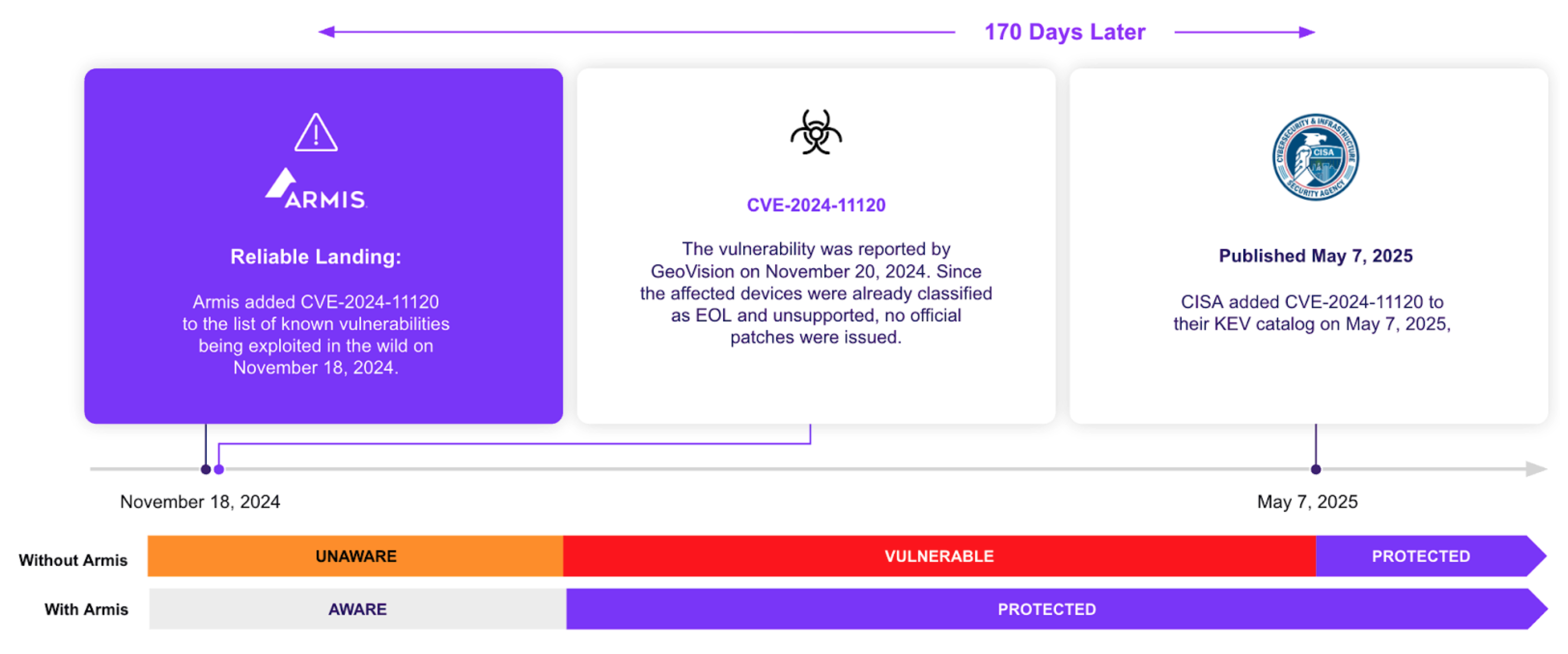
The vulnerability was reported by GeoVision on November 20, 2024. Since the affected devices were already classified as EOL and unsupported, no official patches were issued. GeoVision’s advisory emphasized the critical risk and strongly recommended immediate replacement of vulnerable systems.
Armis CentrixTM for Early Warning, added CVE-2024-11120 to the list of known vulnerabilities being exploited in the wild on November 18, 2024.
CISA added CVE-2024-11120 to their KEV catalog on May 7, 2025, making Armis CentrixTM for Early Warning early by 170 days.

Significance of CVE-2024-11120:
Vulnerable component: The issue lies in the implementation of user input filtering in an unspecified function of the affected GeoVision devices. Due to flawed input validation, there is a lack of proper sanitization of user-supplied input before it is used in system operations, leading to arbitrary system command execution.
Exploitation scenario: Attackers can exploit this vulnerability by sending a crafted payload to the /DateSetting.cgi endpoint of an exposed EOL GeoVision device. CVE-2024-11120 has been observed in active campaigns, notably in a Mirai-based botnet campaign targeting these legacy IoT devices.
Impact and blast radius: As attackers are able to execute arbitrary system commands, exploitation may result in full host system takeover. Additionally, attackers can perform network enumeration and lateral movement within the victim’s environment.
Value of timely awareness: Fast remediation and proactive action, such as replacing the vulnerable EOL GeoVision devices, are essential to reduce the risks associated with this vulnerability. Given the severity and the lack of patches, attackers could rapidly compromise these EOL devices and enumerate the victim’s infrastructure.
Mitigation and Protection:
Proactive defense and workarounds: It is critical to replace your EOL GeoVision devices. If replacement is not possible, disable the devices and monitor for exploit attempts.
Continuous monitoring and updates: Security teams should monitor vendor advisories and remediate issues as soon as they are published. Replace vulnerable EOL devices, monitor suspicious traffic as outlined in the technical details above and in the official advisory, and regularly assess existing security controls.
Stay vigilant and ensure your systems are up-to-date to defend against evolving cybersecurity threats.
Armis Centrix™ for Early Warning is the proactive cybersecurity solution designed to empower organizations with early warning intelligence to anticipate and mitigate cyber risk effectively. By leveraging AI-driven actionable intelligence, Armis Centrix™ provides insights into the vulnerabilities that threat actors are exploiting in the wild or are about to weaponize, allowing organizations to understand their impact and take preemptive action.
Interested in learning more about Armis Centrix™ for Early Warning? Sign up for a demo today!

