Armis Centrix™ for Vulnerability Prioritization and Remediation
Finding risk, prioritizing response, identifying the owner, and operationalizing the remediation lifecycle.
Vulnerability Assessment Tools Leave Critical Gaps
Organizations need to target those vulnerabilities that are most likely to be exploited and negatively impact the business.
Expanding Attack Surface
Today’s organizations are overwhelmed by the sheer volume of vulnerable assets in their environment at any given moment. With every new asset deployed in support of growth, innovation, and efficiency efforts, the enterprise attack surface expands.
Number of Vulnerabilities
There were more than 26,000 vulnerabilities disclosed in 2023. The volume of accumulated vulnerabilities that organizations need to deal with today is measured in the millions.
CVSS Won’t Cut It
Vulnerability scanner output data that only considers the CVSS score (Common Vulnerability Scoring System) leads to teams wasting their valuable time on vulnerabilities that pose little to no risk.
Vulnerability Assessment – Means You are Still Vulnerable
Organizations are regularly faced with a deluge of security alerts, with no clear means to definitively address them. Discovering vulnerabilities is a great first step. But what you do about them is the difference between eliminating risk and remaining exposed. Close the legacy gap between security findings and scaling the remediation process to secure the attack surface.
Armis AI Approach is More than Just Vulnerabilities
Introducing Armis Centrix™ a unified platform for technology risk prioritization and resolution lifecycle management across code, infrastructure, cloud and application findings.
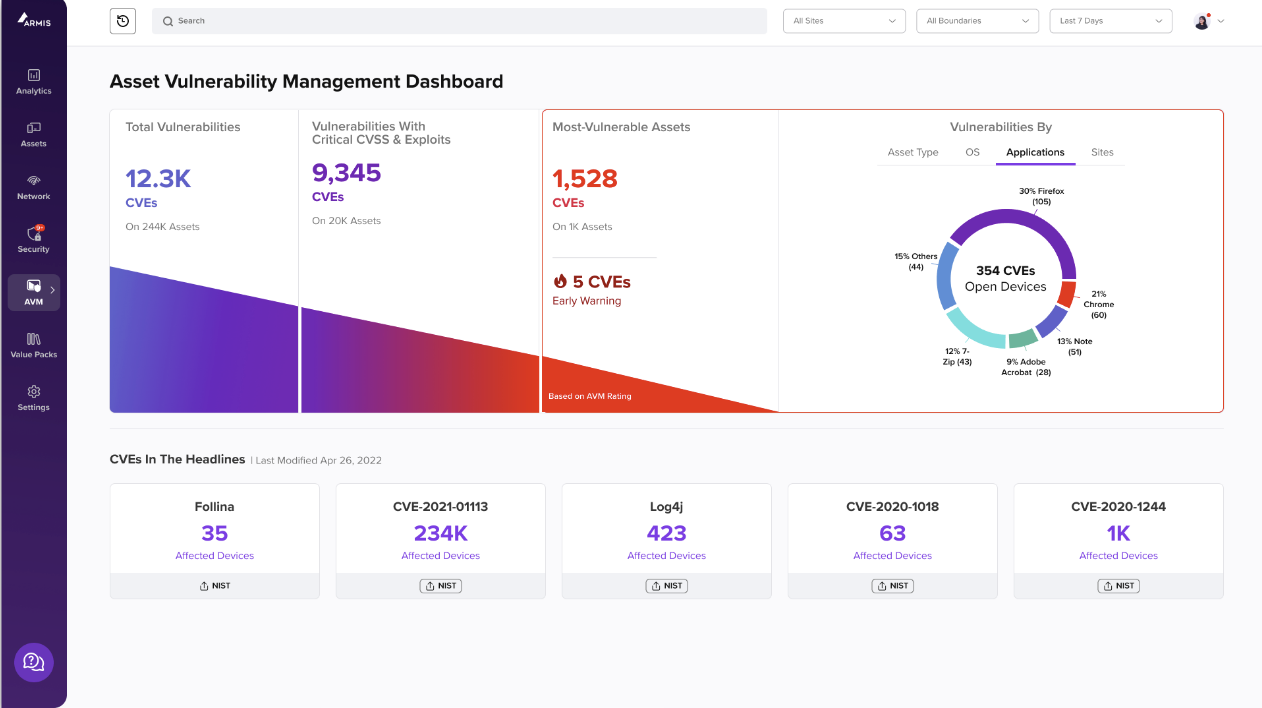
Armis takes a data-centric, AI-driven approach to enable security stakeholders to better identify risks, communicate priorities, assign owners, and collaborate with developers and operations stakeholders to efficiently manage the entire lifecycle of the resolution management process. This approach extends across security findings to encompass infrastructure, code, cloud and application security tools, providing security teams with a consolidated view into security findings and how remediation activities impact overall risk posture that can impact the business.
Armis Centrix™ for Vulnerability Prioritization and Remediation empowers organizations to definitively and comprehensively prioritize manage the remediation of the high volume of alarms and notifications that organizations face. It’s simply not enough to know what threats an organization is facing. Being able to manage them in a prioritized, automated and trackable way delivers a highly cost efficient and highly effective security/compliance methodology that leaves nothing to chance or being overlooked.
How It Works
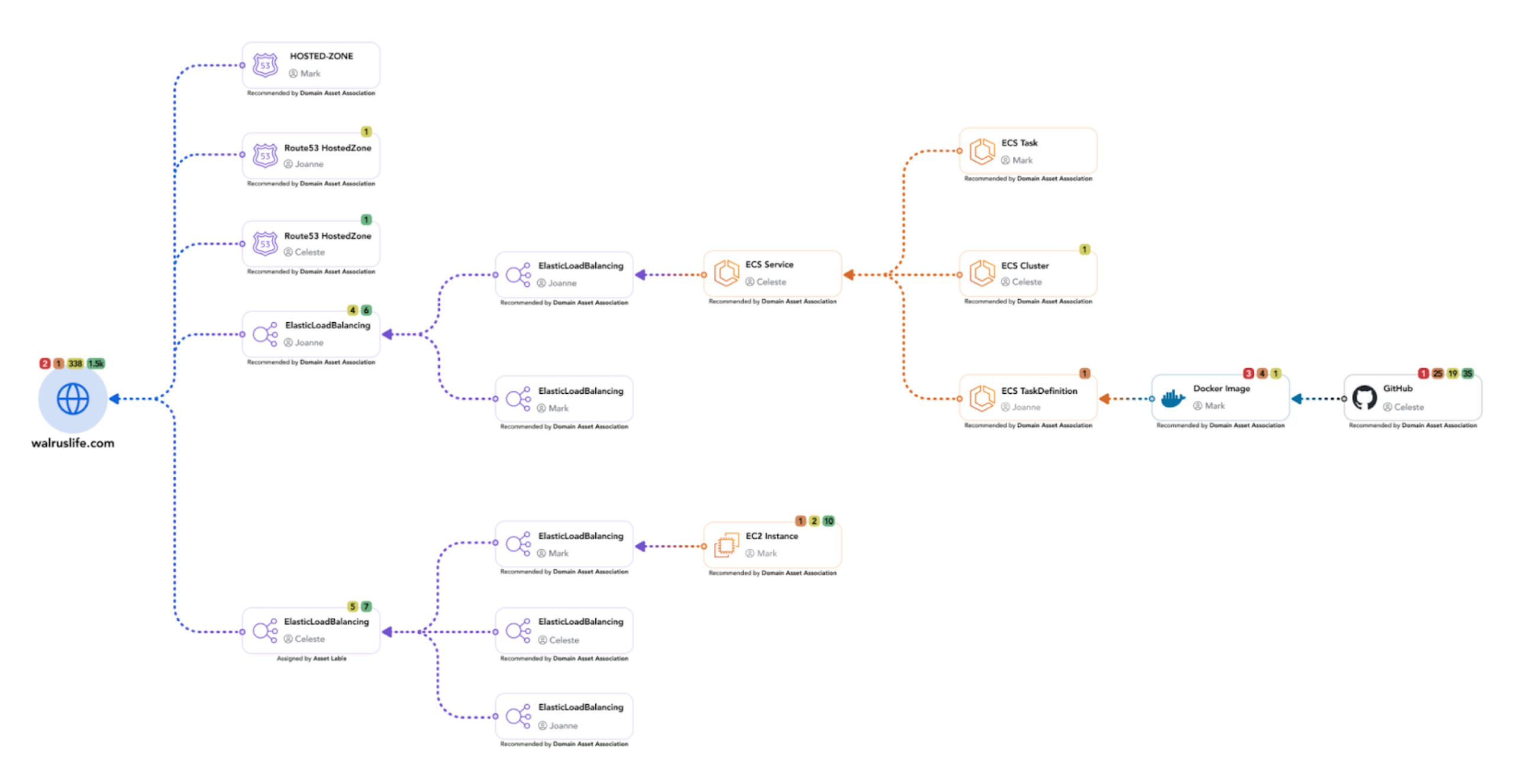
Asset Context and Enrichment
Armis performs a full asset discovery in order to gain deep situational awareness of every device and asset in your environment whether it is physical or cloud based. This inventory is assessed against the Armis AI-driven Asset Intelligence Engine. This unique crowdsourced knowledge base tracks profiles for over 4 billion assets globally. It is continuously updated with the latest information about threats, vulnerabilities and exploits, ensuring you are always up to date.
With Armis’ asset linking capability, security teams gain a systemic and actionable understanding of both the relationship between assets. Identify high-impact fixes using root cause analysis to pinpoint the earliest point in the software development cycle, whether at the code repo or in Infrastructure as Code (IaC) template, that a vulnerability or exposure was introduced. This allows security teams to clearly visualize how assets (and sets of assets) are architecturally related as components of a specific application. An asset can be a physical host, VM, container, cloud resource, service and a code repository. The end result is full context for every asset, along with the option of appending crucial data if information is missing.
Automate & Consolidate
Armis Centrix™ brings strategic order to the deluge of inbound alarms and data by automating risk prioritization and orientation through consolidation of detection tool findings. This is combined with contextualization of the findings through asset intelligence and configurable risk assessment.
Prioritize Based On Business Impact
Armis Centrix™ understands the relationships and dependencies of each asset. Automate risk prioritization and orientation based on the severity of the threat and the criticality of the asset to the business.
Establish Ownership
Armis Centrix™ for Vulnerability Prioritization and Remediation leverages its proprietary AI technology and generates predictive ownership rules and remediation paths to assign fixes. This enables ongoing and highly efficient communication for distributed teams through bidirectional integration with their preferred workflow.
Automate Remediation Workflows
Armis Centrix™ for Vulnerability Prioritization and Remediation automates ticketing and task routing across multiple instances of the same workflow tools, as well as integrations to multiple types of workflow tools within the same enterprise.
Business Outcomes That Deliver
- Cut time spent on identifying owners and assigning tickets by 90%, with custom ticketing rules.
- Reduce findings volume in complex environments by 50-1 with ML deduplication
- Improve MTTR by as much as 90%
- Halved the time for resolution of critical findings, with ongoing improvements in reduction of response times anticipated
- Increase the number of closed findings by 7x over three months, reducing overall threat debt
RumbergerKirk Law Firm Gains Unprecedented Visibility into Assets and a Solid Handle on Potential Risk
Armis Supports Remediation Efforts with Rich, Continually Updated Device Information
Not only does Armis provide extensive and deep visibility into known and unknown assets that connect to the corporate network, it also quickly identifies security gaps and vulnerabilities, which has helped evolve and enhance risk mitigation efforts.
Additional Resources
Solution Brief: Armis Centrix™ for Vulnerability Prioritization and Remediation
Learn how Armis Centrix™ consolidates relevant vulnerabilities and enables security teams to quickly identify and remediate those vulnerabilities that are most likely to be exploited.
Solution Brief: Armis Centrix™ Revolutionizing Security Remediation
Learn why Silk Security is a strategic addition to our mission of providing comprehensive security solutions including advanced cloud security capabilities.
2023 Gartner Market Guide for Vulnerability Assessment
According to Gartner “Vulnerability Assessment solutions identify, categorize and prioritize vulnerabilities as well as orchestrate their remediation or mitigation.” Read the report to see the Gartner report’s recommendations for Security and Risk Management leaders and why Gartner recognizes Armis as a Vulnerability Assessment vendor.
Armis Provides Real Insights into Assets on Ziekenhuis Oost-Limburg’s Network
Armis solves ZOL’s main security challenges by providing real-time visibility and intelligence into their IT, IoT, and IoMT assets and prioritizing their vulnerabilities. Armis was deployed in days, enabling ZOL to address their vulnerabilities and derive value immediately.

